Do you search about the xmlrpc.php file and how you can disable it in WordPress? This article will explain what xmlrpc.php is and how you can disable it.
Communicating with WordPress from applications outside of the WordPress environment via the XML-RPC specification is possible by standardizing a communication method between systems.
Since its origin, this specification has been of great value to the WordPress community. Without it, WordPress would have been isolated from the rest of the Internet.
However, xmlrpc.php has some disadvantages as well. WP REST API has become a vital component of WordPress since xmlrpc.php file vulnerabilities were discovered. This greatly enhances how WordPress interacts with other software programs.
The purpose of this article is to explain what xmlrpc.php is, why this should be disabled, and how you can disable it.
We also suggest you to check our article about the best WordPress security plugins.
What is the xmlrpc.php file?
The xmlrpc.php file is a feature in WordPress that allows remote communication between your website and other web applications. It can also be a potential security vulnerability as it’s an easy target for brute force attacks.
Using HTTP as a transport protocol and XML as an encoding protocol, XML-RPC could standardize the protocols used in these communications.
WordPress was forked in 2003 from the b2 blogging software, which used XML-RPC as an interface. A file called xmlrpc.php resides in the system’s root directory and contains the code for this feature. This file is still available even though XML-RPC is mainly obsolete.
It was the default setting in early versions of WordPress to disable XML-RPC. Since version 3.5, it has been enabled by default to support communication between your WordPress mobile app and your WordPress installation.
Before WordPress version 3.5, the WordPress mobile app could only post content if your site was configured with XML-RPC. This was caused by the fact that the app was not running WordPress; instead, it communicated with your WordPress site using xmlrpc.php.
Additionally, XML-RPC is used to communicate between WordPress and other blogging platforms and between WordPress and the WordPress mobile app.
XML-RPC can be used for pingbacks and trackbacks. It also served as the backend for the Jetpack plugin, which made it possible for self-hosted WordPress sites to become members of WordPress.com.
Because the REST API has now been integrated into WordPress core, we no longer use the xmlrpc.php file. Instead of using this file, you can now communicate with WordPress’ mobile app, desktop clients, Jetpack plugin, and other systems and services using the REST API.
It is also possible to integrate REST API with a wider range of systems, and its flexibility is greater than that of xmlrpc.php. Since XML-RPC has been replaced by REST APIs, you must disable xmlrpc.php on your website to avoid problems.
Why should you disable XML-RPC?
You should be aware that the xmlrpc.php file may expose the XML-RPC enabled vulnerability of your WordPress site to hackers, so you must disable it.
The use of XML-RPC is no longer necessary for communications outside of WordPress. If you wish to keep your site as secure as possible, you should disable it.
It is for this reason that WordPress will always be backward compatible. You should constantly update the WordPress plugins and themes associated with WordPress websites if you are responsible for them.
If XML-RPC is enabled on your website, a hacker can use it as a tool to launch a DDoS attack on your website. They can use the xmlrpc.php module to generate many pingbacks to your site, which can overload the server and cause the website to go down.
Furthermore, xmlrpc.php also sends authentication information with each request, so hackers may be able to intercept this information and use it to attempt to access your website. This brute force attack can allow hackers to execute malicious code, delete code, and even damage your database.
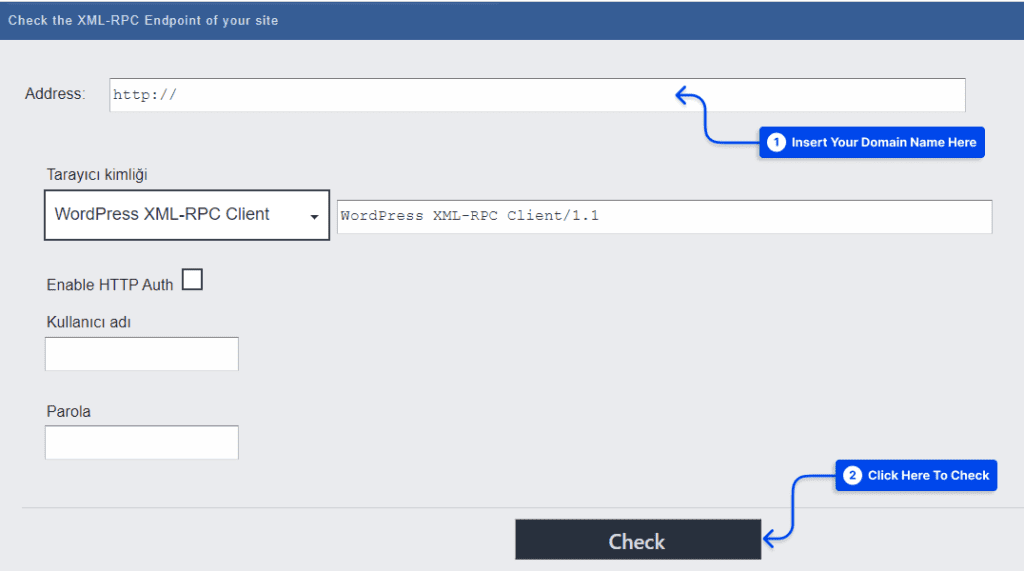
How to check XML-RPC is enabled?
Please click the following link to access the website: WordPress XML-RPC Validation Service.
Once you have entered your domain name, click the Check button.
If the test was successful, XML-RPC will now be enabled, which should be turned off immediately.
Disable XMLRPC Using WordPress Plugins
For various reasons, site owners may wish to disable the XMLRPC functionality. You can use various plugins, such as Disable XML-RPC, to do this.
Disable XMLRPC using the Disable XML-RPC Plugin
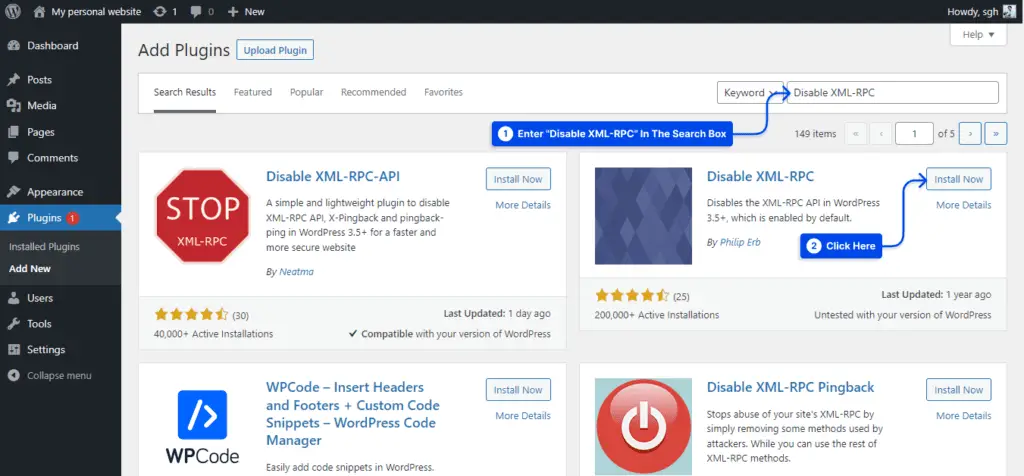
We explain how to use the Disable XML-RPC Plugin to disable the XMLRPC functionality. Please log into your WordPress administration panel.
1. Click on Plugins and then Add New.
2. Enter “Disable XML-RPC” in the search box. Install the Disable XML-RPC plugin after that.
3. Activate the plugin, and you are ready to go. Then, the XML-RPC is disabled.
In this plugin, you can find an XML-RPC Validator that can be used to check whether XML-RPC has been disabled. In the event that XML-RPC has been disabled, a failure message will appear. If not, you can disable it with this plugin.
Configure XML-RPC and REST API Activation with a Plugin
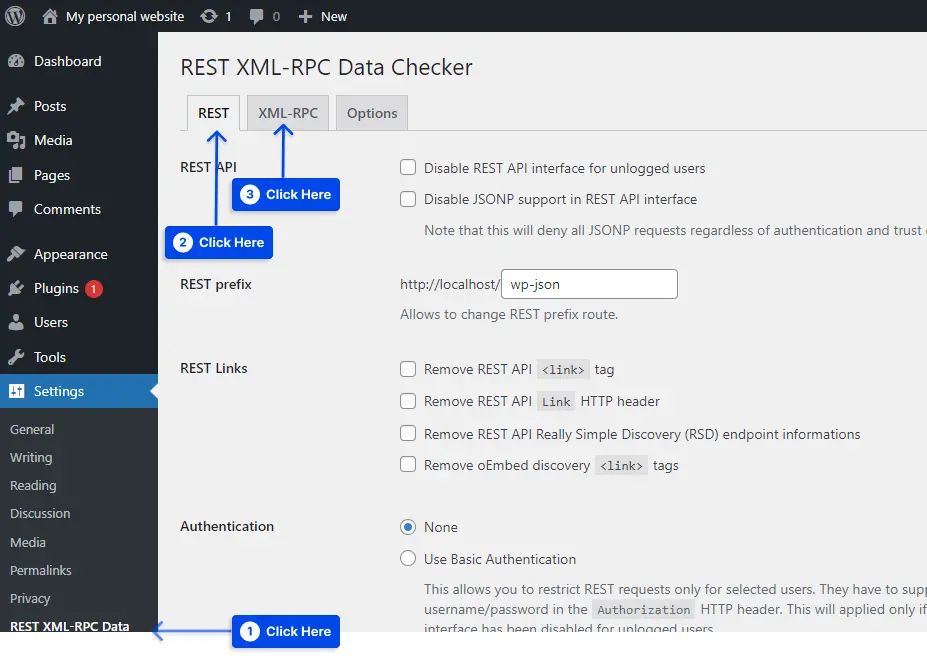
The REST XML-RPC Data Checker plugin allows you to configure the REST API and the xmlrpc.php on your website more fine-grained manner.
After you have installed and activated the plugin, click the XML-RPC tab after clicking the REST XML-RPC Data Checker tab in the settings.
Through the plugin, you can specify exactly which features of xmlrpc.php are enabled on your site. It is also possible to completely disable it. There is also a tab in the plugin that allows you to control the REST API if you choose to do so.
Disable XMLRPC Without a Plugin
If you prefer not to add another plugin to your website, you may disable xmlrpc.php using a filter or your .htaccess file. Let’s consider both options together.
Disable xmlrpc.php via a Filter
By using the xmlrpc_enabled filter, it is very easy to disable the xmlrpc.php. You should add this function and make it active on your website:
add_filter( 'xmlrpc_enabled', '__return_false' );The function could be added to the theme’s functions file. A .htaccess file may also be edited using either cPanel or FTP, depending on whether you are connected to a hosting provider using Apache.
WordPress’s __return_false function returns the boolean false condition. This filter only blocks operations that require a logged-in user.
It must be deregistered from all methods to disable all operations of the XMLRPC server. In order to achieve this, you need to hook into the xmlrpc_methods filter.
add_filter( 'xmlrpc_methods', 'betterstudio_remove_xmlrpc_methods' );
function 'betterstudio_remove_xmlrpc_methods( $methods ) {
$methods = array(); //empty the array
return $methods;
}
The xmlrpc.php file creates an object of class wp_xmlrpc_server when a request is made. Within the wp-includes folder is a class file containing a property called methods.
The methods property includes an array of names of functions that can be accessed via XML-RPC requests.
The function is returned with an error message when it is not included in this array. Thus, if you empty the array, you are assured that you will not be able to use any functions.
Disable XML-RPC using .htaccess
Disabling the XML-RPC using .htaccess include a few simple steps. This is how you can disable xmlrpc.php .htaccess:
- You may use FTP or File Manager to navigate to the root directory of your website.
- You should open the .htaccess file.
- You will need to add the following code to your .htaccess file:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
</Files>
xxx.xxx.xxx.xxx can be replaced with the IP address you wish to grant access to xmlrpc.php. If you wish to remove xmlrpc.php from WordPress entirely, you may remove this line.
Disable XMLRPC in Apache/Nginx
Disabling XMLRPC in Apache/Nginx can also be simple process. The following code should be added to the Apache configuration file to disable xmlrpc.php:
< VirtualHost >
----------
< files xmlrpc.php >
order allow,deny
deny from all
< /files >
< /VirtualHost >Using the following code in the Nginx configuration file, you can disable xmlrpc.php:
server {
-----------
location /xmlrpc.php {
deny all;
}
}How searching for and find XML-RPC attacks in different Linux distributions?
If you are searching for XML-RPC attacks in different Linux distributions, you can use the following commands to stop xmlrpc.php attacks:
A CentOS server with Apache installed:
# grep xmlrpc /var/logs/httpd/access.logWith Apache on Ubuntu:
# grep xmlrpc /var/logs/apache2/access.logFor Nginx-based servers:
# grep xmlrpc /var/logs/nginx/access.logFor cPanel-based servers:
# grep xmlrpc /home/username/logs/access.logYou would receive the following output if the previous commands were executed on a WordPress site that is under attack:
POST /xmlrpc.php HTTP/1.0” 200 674 “-” “Mozilla/4.0 (compatible: MSIE 7.0; Windows NT 6.0)When to keep the XML-RPC.php file enabled
There are a few situations in which it would be advantageous to enable XML-RPC, and these are some of them:
- If the REST API is unavailable when you have an old website that cannot be updated to version 4.4 or higher for whatever reason.
- A program cannot access the REST API on the website you are using to communicate with it.
- In order to integrate some third-party applications that require XML-RPC to work.
It should be noted, however, that none of the above criticisms are sufficient reasons for continuing to use XML-RPC and xmlrpc.php exploit.
The only reason WordPress has it is that it is backward compatible; as a result, you will only want to use it if you are using an outdated version of WordPress.
For those who wish to keep their site current and support the latest software version, xmlrpc.php should be disabled.
Testing XML-RPC Functionality in WordPress
Additionally, you can use the WordPress test option to verify that your website has been successfully disabled from receiving XML-RPC requests.
For this purpose, you may download the WordPress Mobile App to your phone. There are Android and iPhone versions of this application available. After installing the app on your device, tap on Enter your existing site address to begin using it.
You are done if you see the error message that XML-RPC services are disabled on this site. This is a WordPress xmlrpc.php 403 forbidden message.
Conclusion
The XML-RPC specification was developed prior to the creation of WordPress to allow communication with external applications and systems. Several security flaws exist in this specification, which could make your website vulnerable to attacks.
The REST API allows your site to communicate with other programs, making it possible to disable xmlrpc.php without concern. If you wish to increase the security of your website, follow the mentioned steps to do this.